Authentication
Authentication and encryption on the network
© copyright mowais.seecs.nust.edu.pk
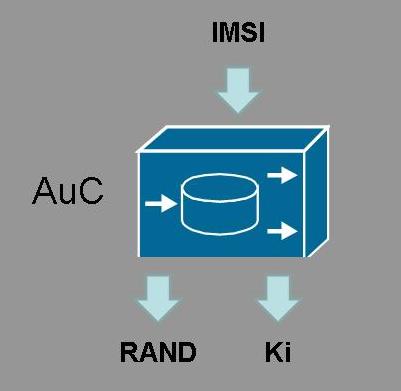
The Authentication Centre (AuC) provides 2 functions to the GSM network. Firstly it stores the key (Ki) associated with the SIM. This key is only stored in the AuC and SIM and provides the mechanism for encrypting data on the wireless network. Secondly the AuC will use the key to generate the 128bit RAND random number used in the authentication and encryption processes on the network.
- When the MS require access to the network it needs to be authenticated. It requests access from the MSC which then forwards the IMSI to the HLR
- The HLR will check that the IMSI is valid and forwards this to the AuC whih is usually located local to the HLR.
- The AuC will find the key (Ki) and generate a 128bit random number (RAND)
- The AuC uses the A3 32bit algorithm to generate the signed response (SRES) from Ki and RAND.
- The AuC will also generate the encryption key (Kc) using the 64bit A8 algorithm
- The triplet(s) (RAND, SRES, Kc) and returned to the HLR and to the MSC
- The MSC stores the triple and sends RAND to the MS, which repeats the A3 and A8 algorithms to generate the SRES and Kc
- SRES is sent to the MSC and if this is the same as the AuC generated SRES then the MS is authenticated. If so Kc is passed to the BTS to allow allow for encryption of the data over the wireless network
- When data is sent, the DATA and Kc are input to the A5 algorithm and encrypted. This data is send over the wireless network. The receiver again uses the Kc to decrypt the data
Note that in this process none of the keys are passed over the network in any format. Also note that it is only the wireless aspect of the network that is encrypted and not the back haul network.
*u* ©mobilephonetechnology.co.uk all rights reserved 2017- 2025



